A few days ago, I earn the CRTO badge from Zero-Point Security.
While I was passing the OSCP, I watched almost all videos from Andy Li’s YouTube channel to accompany me during the journey, and this one in particular caught my attention ⬇️
It was the first time that I heard about a Red Team certification, so I decided that it would be my next goal once I will be done with OSCP.
CRTO stands for Certified Red Team Operator.
The exam involves compromising at least 6 out of 8 machines, in 48 hours which you can split in a four days window.
TL;DR ➡️ I definitely recommend the course. I failed at my first attempt and succeeded at my second one (three days after). In this blog post, I’ll tell my story and share some advice. Here are some things you will get if you decide to take this training:
➡️ a LIFE TIME ACCESS to all the updates of the course
➡️ an instance of Splunk to look at the indicators you may leave
➡️ and the opportunity to use Cobalt Strike C2 without breaking the bank
I am neither a native speaker nor a security expert. Please do not hesitate to correct me if you think I’m wrong. There is a
Disquscomment section below.
- 🏴☠️ Red team engagement vs Penetration test (Thoughts on real-world threat actors)
- 📖 Zero-Point Security - Red Team Ops course
- 🧑🏫 Recommendations for CRTO aspirants
- 🧑🎓 My journey
- 📚 Notion Templates for note taking
- 🛣️ What I want to study next?
- 🌐 Useful resources
🏴☠️ Red team engagement vs Penetration test (Thoughts on real-world threat actors)
According to Joe Vest and James Tubberville in their (excellent) book “Red Team Development and Operations: A practical guide”:
Red Teaming is the process of using tactics, techniques and procedures (TTPs) to emulate a real-world threat, with the goal of measuring the effectiveness of the people, processes and technologies used to defend an environment.
Tactics are the technical goals a threat may use during operation.
Examples: Reconnaissance, Bypassing Defenses, Privilege Escalation, Persistence, Exfiltration and so on.
Techniques describe the actions threats take to achieve their objectives.
Examples: Password Spraying, ARP Cache Poisoning, Exploiting SUID/SGID binaries, SID-History Injection, etc.
Procedures are the technical steps required to perform an action.
Example: for reconnaissance, attackers might collect information about the target, identify key individuals and enumerate externally exposed services.
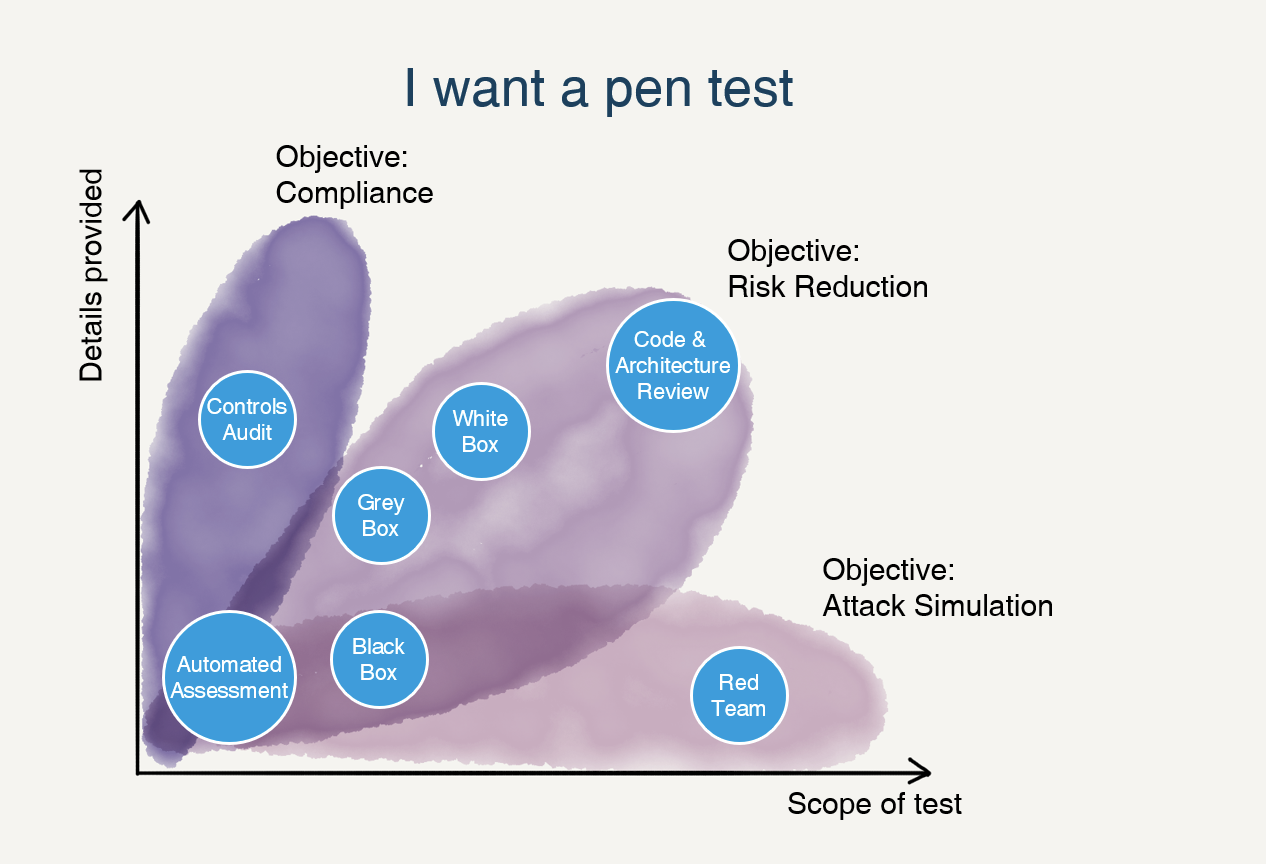
The differences in terms of scope and provided details between a Pentest and a Red Team engagement can be shown in this chart of outpost24:
It is well explained in this video of thehackerish ⬇️
The only thing I would add is the following:
Contrary to what I thought, real world threat-actors do not necessarily follow the steps:
1️⃣ scanning for vulnerabilities → 2️⃣ exploit → 3️⃣ profit.
In reality, they take several steps to get an initial compromise, establish persistence/command and control, evaluate weaknesses, move laterally and perform situational awareness in order to achieve their goals.
📖 Zero-Point Security - Red Team Ops course
When I went through the course material, I really felt that the instructor (@RastaMouse) made a huge effort to summarize each concepts.
It is well written, clear, concise, the information are easy to digest.
Generally, 1 page = 1 new notion (for example COM Hijacking or “The Printer Bug”).
It is presented in such a way that you’ll have a short description of the concept, tools and techniques along with useful command lines and OPSEC consideration notes.
I don’t want to re-write the whole course syllabus but you’ll learn a lot about Domain enumeration, Phishing, Delegation types, Bypassing defenses (AV, AppLocker, PowerShell Constrained Language Mode), Lateral Movement/Pivoting, MS SQL abuses, LAPS, User impersonation and much more.
The day I finished my exam, I received a mail telling me that the RTO course was moved from Canvas to the Thinkific platform.
I took a look at it and it seems much “prettier” and pleasant to move from one module to another quickly.
The nice thing about Canvas was the “Search Tool” 🔍 to look for keywords or specific tools/command lines.
I didn’t find a similar search function on Thinkific but maybe I didn’t investigate enough 🤷.
The lab is accessible via SnapLabs so you can do everything in your browser.
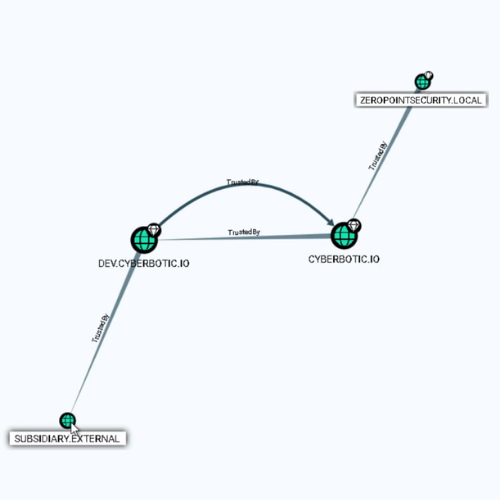
A Kali and a Windows VM are available (for both the exam and the training lab) to attack an Active Directory composed of three forests.
🧑🏫 Recommendations for CRTO aspirants
1️⃣ Follow the modules in the order they are presented to you. The lab is created in a way that some steps depends on others.
2️⃣ As you go through the course, don’t wait for to see an “exercise” section to reproduce what you just learned.
3️⃣ Take effective notes and as always build you own cheat sheet.
4️⃣ Once you booked your exam, the Threat Profile that you need to emulate, is directly available in SnapLabs! Download it and build your custom C2 profile for Cobalt Strike, test it on the training lab and ensure it works. This will save you a lot of time!
5️⃣ Sometimes you can feel lazy about reproducing some parts of the course in your lab. My suggestion is: as long as you’re able to understand it and reproduce it quickly, if this is not a step required to move forward, take some notes and skip it.
6️⃣ Even if you’re already familiar with some tools, do not hesitate to experiment with the different options they offer (Mimikatz, Rubeus, etc.) There can be different ways for doing the same thing.
7️⃣ Look at the Splunk logs and try to understand the evidences you are letting behind you. It’s an invaluable experience that you have Splunk and Cobalt Strike already set up for you to experiment.
8️⃣ It’s better to have some knowledge about Windows Active Directory and Kerberos before jumping in.
I recommend doing the Section 4 of the Offensive Learning/Comptia Pentest+ path on TryHackMe.
9️⃣ Read some reviews, they are gold mines!
🔟 Think “Persistence” in the training lab, even if this is not mentioned.
🧑🎓 My journey
🎒 Background
I have no prior professional experience in Active Directory Penetration test.
I only learned a few stuff about Kerberos *roasting, Silver/Golden Tickets, and how AD basically works while doing my OSCP prep.
I just graduated and didn’t start a job in infosec yet.
⚗️ Lab
I spent 18 hours in total in the lab, watched every single video, took as many notes as I could. Basically, I rewrote the whole course in my own words. I also built a new cheat sheet with all the concepts, steps and command lines. Unfortunately, this time, I will not share it with you cause this would involve me leaking course content.
⏱️ Exam
❌ First attempt
As I mentioned before, I failed my first attempt. Here is what happened:
- It had already been over a month since I had started the course, I had just finished reading each module and had taken a lot of notes.
- I felt that I was not ready for the exam but rather than taking more time to redo some exercises, I preferred to try the exam directly.
- I was convinced that even if I fail, I would know what to expect for a future attempt.
- The night before the exam and throughout the week, I was sick (maybe Covid?)
- I spent 2-3 days to get my custom C2 profile working BECAUSE OF ONE LINE 🤯!!!
c2lintdidn’t warned me about the error, but it was a very dumb one.- I should have tried writing and testing my custom C2 profile before taking the exam.
- Once the C2 profile was no longer a problem, everything went smoothly and I collected 4 flags in a short amount of time.
- Then I was stuck (maybe because I was too much concerned about OPSEC)
- I couldn’t use all the hours dedicated for the exam because I had to travel ⬅️ assuredly because of a bad time management
✅ Second attempt
A few days after my failing experience, I took some time to reread all my notes, go through each course module to check if I missed some interesting command lines.
The second attempt was more “enjoyable” because I knew how to get to the 4th flag quickly.
Nevertheless, I still took the time to do proper enumeration and carry out several post-exploitation activities.
I think the way I managed to get the fifth and sixth flag was not the intended path.
The reason why I am saying this is because it wasn’t as elegant as the previous techniques and above all, it had a pretty bad OPSEC. I’m almost sure that it was not the way it was supposed to be done. However, I still managed to compromise the different machines and achieve the objective of the exam.
🏅 Receiving the badge
My 4 days window for the exam ended at 10:30 AM on February the 1st. I knew that I passed because on January the 30th, I collected the 6 flags required to pass the exam.
At 12:59 PM the same day, I received an email from badgr.

💶 Cost (€ / £)
- Course: 409,32 € = 349 £GB
- 40 hours of lab access: 58,64 € = 50 £GB
- I spent 18 hours in total and I plan to continue to use the hours I have left to experiment new things.
- Second exam attempt: 119 € = 99 £GB
🤔 Final thoughts
- I know for sure that the course material is a resource that I will often return to.
- Attackers should be creative, try to bypass defense mechanisms and find their way in. There are multiple methods to achieve an objective.
- Besides the fact that I have acquired a lot of technical knowledge throughout this training, I feel that the main lesson of the course is: “there is always a way”.
- I failed the first time because I wasn’t thinking outside the box, I wasn’t enough creative!
- Most of the things we exploited in the lab were not vulnerabilities (such as Eternal Blue or SambaCry) but misconfigurations, Kerberos implementation with Microsoft specifics, and features of Active Directory.
- For example: the Golden Ticket technique is not a vulnerability in itself.
Cobalt Strike was so cool to use. I wish I can bring it with me for each challenge/engagements I will face in the future.
I understand why it is a such popular tool. Nevertheless, it remains an expensive tool and I need to familiarize myself with other C2 such as Covenant, PoshC2 and much more from the C2 matrix!
- Red cannot exist without Blue. The goal of an operator is to bring value to the organization.
📚 Notion Templates for note taking
🛣️ What I want to study next?
- Sektor7 Malware Development Courses
- C2 Development Course by Zero-Point Security
- OSEP
- HackTheBox Pro labs
- TCM courses (Practical Phishing engagement, Movement, Pivoting and Persistence, etc.)
- Improving my Reverse Engineering skills via Zero2Auto course
- Taking a look at Blue Team Labs and Cyber Defenders
- OSWE, OSED and OSWP
🌐 Useful resources
🧐 Reviews
thehackerish - Certified Red Team Operator (CRTO): 🧐 HONEST Review 🧐
0xash - Zero-Point Security’s Certified Red Team Operator (CRTO) Review
Andy Li - Certified Red Team Operator (CRTO) - Exam Experience
Operate Like You Mean It: ‘Red Team Ops’ (CRTO) Course Review
Malleable C2 profile
Understanding Cobalt Strike Profiles - Updated for Cobalt Strike 4.5
[RED TEAM] Cobalt Strike 4.0+ Malleable C2 Profile Guideline